We are approaching a moment in history where technology is becoming the driving force for convenience in our lives. In a way, this is both a wonderful thing and a prelude to a complex series of nightmares. The way you proceed when browsing the internet weighs heavily on whether your experience will be pleasant or disastrous. The typical Internet user may understand what social engineering is, but probably doesn’t know how to apply that knowledge to constructing a proper defense plan against attempts to compromise their data.
To help you make your own personal security policy, instead of focusing so much on specific problems, we’re going to tackle the entire issue of security with a couple of broader pieces of advice.
Assume Hostility
Whenever crossing unknown territory, assume the worst. Do not misinterpret this as scare-mongering, though. All we’re saying is that if someone sends you a link — even if it’s someone you know — always assume that the link could be malicious. Yes, people you know and love can send you scammy links. This isn’t because they suddenly decided to be mischievous. Rather, it’s more likely that the person who sent you the link isn’t even aware that he/she did it. Anyone (even computer experts!) could be infected with a piece of malware that automatically logs onto their Facebook account (for example) and starts dishing out sketchy links to everyone on their friends list.
Signs to look out for:
- Atypical behavior (e.g. a normally calm person suddenly appearing excited in messages just before posting a link).
- Excessive use of URL shorteners (bit.ly, etc.).
- Repetition (sending the same link, or a similar link, periodically without regard to your replies).
- References to an event you haven’t participated in (e.g. “Dude, you were so wild at that party!”).
If you see enough signs that people may be infected with malware, kindly send them a message telling them that their system may be compromised.
If It Seems Too Good to Be True, It Probably Is
Many people have heard of the Nigerian Prince scams. Those who don’t know about it, or don’t fully understand it, should definitely read this! The Nigerian Prince scam involves a person who sends an email saying that they have some large sum of money in store for you. There’s a problem, though. For you to receive your inheritance/escrow fund/whatever, you have to pay a transfer fee. If you pay this fee, you’ll never hear from this person again. The Prince runs with your money and showers himself with your riches.

This is known as a Nigerian Prince scam because, as the name suggests, the entire practice of scamming people via email was popularized in Nigeria by wannabe social engineers who do this for a living. The scam doesn’t necessarily have to involve a prince. I’ve received emails regarding a deceased long-lost relative (from a country that my family came from, no less!) whose estate was to be inherited by me.
Signs to look out for:
- Claims of extraordinary sums of money (in the six-figure and above range).
- The need for a transfer fee (which, in real life, could be paid for with a part of the money, if it even existed) or some other payment in order for the transaction to take place.
- Horrible command of the language they are speaking to you with.
- The offer was completely unexpected (out of the blue).
Your Door Needs More Locks
For decades, service providers on the web have used password authentication to protect user accounts. This has become such a norm, that most of us accept it unquestioningly. The username and password have become the ubiquitous go-to way to log in to anything. However, security isn’t just about how strong your password is; it’s also about how many layers of security you add on top of that password.

Enter the world of two-factor authentication. Google, Yahoo!, Facebook, and Apple have been doing it for a while now. Two-factor (sometimes referred to as “two-step”) authentication puts an extra lock on your account. Instead of being protected by just a password, you get to add something else to it. It could be a one-time password delivered via SMS to your phone number or something more complex like a token device. You may find this to be quite a hassle, but it is very easy to use when you get used to it. Wherever it’s available, you should enable two-factor authentication!
Happy National Cyber Security Month!
Let’s make October a month in which we take the time to make ourselves safer! Share this article, spread the word, ask questions (no matter how dumb you think they are), and comment if you’ve got something to add!
Security advice provided with the aid of SingleHop, hosting IT infrastructure and cloud computing provider.


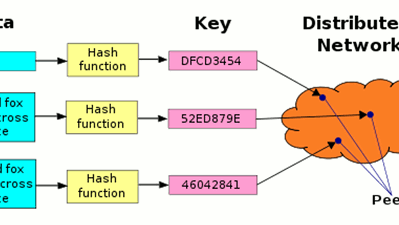



Comments on " A Beginner’s Guide to Not Being Compromised on the Internet" :